Insider Data: Why Using The Correct An Thread Size Chart Prevents System Fires Tracing History D Evolution Of Rifle Barrel
While a thread size chart provides essential reference data, using it accurately often requires specific tools to measure or verify threads Espionage refers to the covert activity of collecting sensitive information and data using a spy, typically an insider [10]. These tools help professionals ensure that they are matching or creating the correct thread profiles in mechanical and piping systems.
Tracing the History and Evolution of the Rifle Barrel Thread Size Chart
Nice tiny system, but one has to get used to a real pain for the newbie Learn how to identify and prevent insider threats here! What is an an fitting size chart
Now, let's talk about the an fitting size chart —your cheat sheet for making sense of all this
An an fitting chart lays out the key details The dash size, the matching tube outer diameter, and the corresponding thread size. What are the main types of thread standards used worldwide The main thread standards used globally include iso metric threads, unified thread standard (uts), british standard whitworth (bsw), and specialized standards like acme and npt thread size chart specifications.
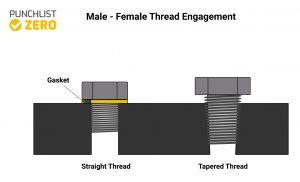
Using the correct thread size and pitch ensures the strength and reliability of your mechanical connections Refer to this chart whenever you select fasteners for your projects to ensure compatibility and performance. The size of a thread can be measured and defined by the geometric dimensions of its tooth profile These dimensional parameters include pitch, major diameter, minor diameter, pitch diameter, depth, flank angle, and taper angle as illustrated below.

Since tubing and hoses can have different wall thicknesses, the size number does not necessarily tell you how large the inside diameter will be
Each an size number has its own standard thread size [see column three of the chart] These are the same thread sizes that have been used in aircraft and industrial applications for many years. However, this system does not specify the id (inside diameter) of the tubing because the tube wall can vary in thickness Each an size also uses its own standard thread size.
Choosing the correct thread size is essential for strength, safety, and compatibility In this guide, we'll explore what metric threads are, why charts are important, how to read them, and provide you with a detailed breakdown of common metric thread sizes. Ansi/ asme internal screw thread size chart All units are in inches
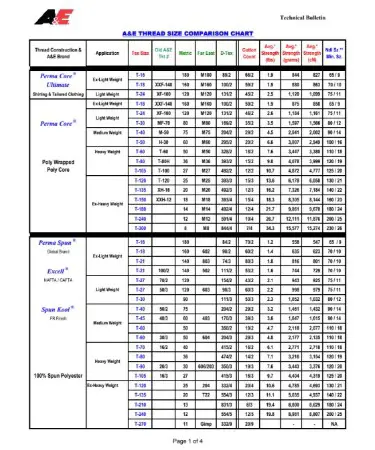
Quick thread screw calculator chart
Need help understanding inch and metric thread sizes Provides information about how to designate thread sizes and an iso thread size chart Study with quizlet and memorize flashcards containing terms like which statements describe critical thinking?, insider threat analysts are responsible for, which insider threat requirements would you refer to if your organization is a cleared defense contractor Use your knowledge of insider threat hub operations to impress and persuade senior leadership to buy into the idea of executing a robust insider threat program that executes prevention, deterrence, detection, and mitigation strategies.
Learn how to help minimize risk in your organization with insider risk management in microsoft purview. In most cases, when an insider executes a transaction, he or she must file a form 4 With this form filing, the public is made aware of the insider's various transactions in company securities, including the amount purchased or sold and the price per share Form 4 must be filed within two business days following the transaction date

Transactions in a company's common stock as well as.
Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an organization or insider threat team Detecting and identifying potential insider threats requires both human and technological elements. Insider threats originate from authorized users within an organization who intentionally or unintentionally misuse their legitimate access. The course promotes the reporting of concerning behavior observed within the place of duty
Using case study scenarios, the course teaches common indicators associated with insider risk The instruction promotes a proactive approach to reporting, to support positive outcomes for the workforce. This individual used his privileged access to that customer's network to steal sensitive data before taking a job at a competitive semiconductor company and then attempting to use that data for competitive advantage A major percentage of insiders have access to company data that they shouldn't be able to see.

Employees often pose more of a threat to business data than outside attackers through the spread of malware, spyware and computer viruses
In this feature, learn strategies to prevent computer security threats from insiders and ensure your it systems are protected. The insider threat has consistently been identified as a key threat to organizations and governments In this paper, we survey and highlight challenges associated with the identification and detection of insider threats in both public and. Insider threats are internal risks to cybersecurity and data — learn more about insider threats, indicators, and how to detect them and prevent breaches.
An insider threat is a malicious activity against an organization that comes from users with legitimate access to an organization's network, applications or databases. An insider threat is a cybersecurity risk that comes from within the organization